- 25 Apr 2024
- 2 Minutes to read
- Print
- DarkLight
- PDF
Granting access to your Google Cloud Storage Source
- Updated on 25 Apr 2024
- 2 Minutes to read
- Print
- DarkLight
- PDF
This article will describe the steps for a Provider to configure Bobsled access to a Google Cloud Storage bucket to be used as a source in Bobsled. For more information on the Google Cloud Storage Source, please visit:
Google Cloud Storage Source: Google Cloud Storage Source
High Level Overview:
Prerequisites
To configure Bobsled access to the bucket, your account must have the sufficient permissions to create policies and assign roles in Google Cloud Storage.
If your GCP restricts domains that can access resources, you must allow the Bobsled domain.
To add the Bobsled domain to your organization policy, you will need the Directory Customer ID from the Bobsled App, visit Menu > Manage > Settings .
Please visit Add domain to organization in GCP and follow the steps to allow the Bobsled domain.
Granting access to your bucket
(1) Create a Custom Role
1. Log in to the Google Cloud Platform Console as a project editor
2. From the Home dashboard, select IAM and admin > Roles
3. Click Create Role
4. Enter a role name and a description for the custom role(e.g. Bobsled GCS Access Role, Custom role for Bobsled to access the required data in GCS buckets)
5. Click Add Permissions button
5a. Assign the following permissions:
storage.buckets.get
storage.objects.get
storage.objects.list
6. Click Create

(2) Assign Custom Role to Bobsled Service Account in the Bucket
Before you start this step, you’ll need the Bobsled Service Account Email address. This can be found on the Data Sources page in the settings of your GCS source in the Bobsled app. In the app, visit Data Sources > GCS Source > Edit
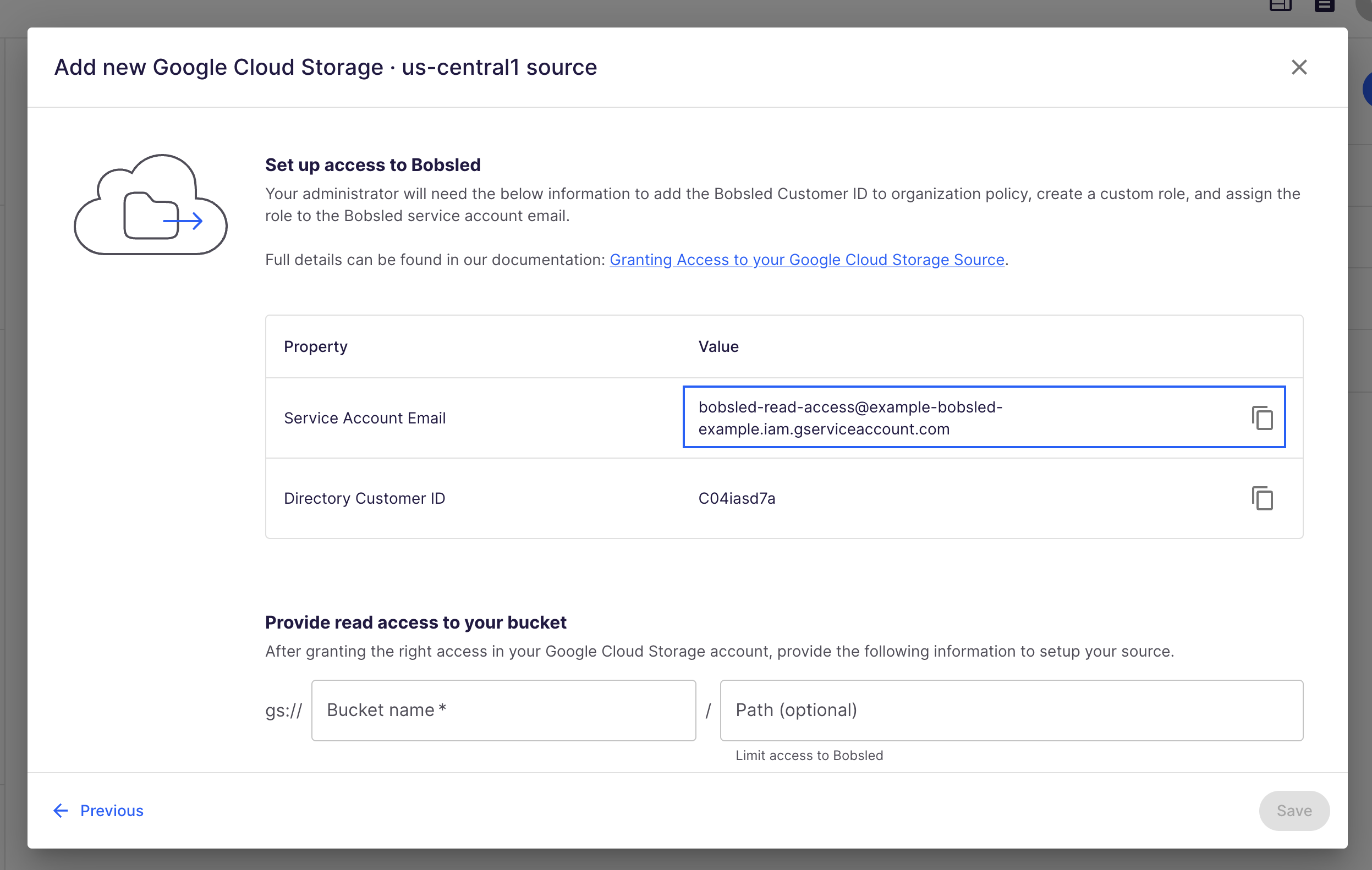
1. Log into the Google Cloud Platform Console as a project editor.
2. From the Home dashboard, choose Cloud Storage > Buckets
3. Find the bucket you want to grant Bobsled Access to and click on the ellipses to the right of the bucket's row. Select Edit Access.
4. Click the Add Principal button.
5. In the New principals field, paste in the Bobsled Service Account Email address and select it from the returned options.
6. Select the Role drop down. Under the Custom tab, choose the Bobsled custom role you created in the pervious section. (e.g. Bobsled GCS Access Role)
7. Click Save. You should see the role added under the Storage Object Viewer role dropdown.
For KMS Encrypted Buckets Only
(3) Grant Bobsled Service Account permission on Cryptographic Keys
Log in to the GCS Console as a project editor.
Navigate to the Home dashboard. Choose Security > Key Management
Select the key ring that is assigned to your GCS bucket.
Click Show Info Panel in the upper-right corner and click add principal button.
In the New principals field, search for the Bobsled service account
From the Select a role dropdown, select the
Cloud KMS CrytoKey Encryptor/Decryptorrole.Click the Save button.
